Building a Robust and Secure PC Ecosystem in windows 11 and windows 10
Building a Robust and Secure PC Ecosystem
You may have heard the term “prevention is better than cure,” which is mostly attributed to the Dutch philosopher Erasmus around the year 1500. Over the years, the phrase has been widely adopted by healthcare but also has significance when it comes to Windows 11 troubleshooting… hear me out on this one.
When problems occur with PCs, you generally have two options, to reimage the PC or to try and find and fix whatever is the cause. If you choose the former option, then you’ll get a quick initial fix, perhaps just 20 minutes reimaging the PC, but then you’ll have a far longer period of either, depending on which reimaging route you take, downloading a ton of Windows and app updates or reinstalling all of your apps and software from scratch.
If you go down the troubleshooting route, which of course is what this book exists to help you with, then the initial fix period will be longer, but the overall process of getting the PC back in full service should be less than the reimaging route. There are no guarantees with this depending on the type of problem you’re facing, as it could turn outto be a real head-scratcher, but you’re up for a challenge, right?
Where prevention is better than cure comes into play is in trying to mitigate the problems to begin with and make sure that nothing ever goes wrong with the PC in thefirst instance so you don’t need to troubleshoot problems at all. Of course, this is anoxymoron as the very nature of PCs with their near infinite combinations of installedsoftware, hardware, peripherals, and connections mean you can never fully mitigateevery problem that will occur, and frankly it would be folly to assume that you can.
Setting up your PCs though in a robust way is always good practice though, and it would be remiss of me to not discuss how to avoid problems in the first instance as part of a troubleshooting book.
Understanding System Restore
Back in the earliest days of my life as an author, I was attached to a book about Windows 8 that I soon afterward was booted off. There were problems here from the beginning, largely because the book was to be written with a specific “voice” that was used in the series that I had difficulty conforming to (you might have already guessed I’m fond of going off on tangents and slipping in jokes, quotes, and anecdotes like this one whenever I can).
The other issue for me though was the co-author I had been assigned. This author was insisting the book start with a section called “Safety First with System Restore.” This stuck in my mind afterward as it started one unholy argument.
In essence, my co-author was quite right; making sure System Restore was working on a PC is a great idea. Where I believed they were wrong however was that (A) the book wasn’t about troubleshooting, rather being a beginner’s guide, and (B) that they wanted us to tell the reader that the very first thing they should do was to create a System Restore point they could go back to if they ever encountered a problem.
System Restore was of course (as he slips gently into another anecdote) first introduced with Windows Me which was released in the fall of 2000. It was widely derided in the days before Windows Vista as a place where viruses and malware would go to hide, ready to pounce again the moment the system was restored, which back in the days of Windows Me was frankly a lot.
Windows Vista was of course the operating system that introduced User Account Control (UAC) which was horrendously intrusive in its first guise, but successfully blocked malware from making changes to a PC that could affect anything other than just the currently signed-in user’s desktop experience. Until this point, the first thing I did on any PC was to turn System Restore off, but with Vista and UAC, it at long last became useful.
So where does this bring us to with the argument over the Windows 8 book and why does it matter? What System Restore does is that it creates a snapshot of critical system files such as the Registry and parts of the Windows kernel whenever a change is made that could cause the PC to become unstable. This includes installing a new piece of win32 desktop software (it doesn’t kick in with Microsoft Store apps) or when a Windows Update is installed.
System Restore reserves a small percentage of the disk, usually between 2% and 5% in which it keeps its backups. This means that if a lot of activity takes place on a PC, such as downloading a lot of updates and installing a lot of software, previously captured restore points are deleted in order to make space for a new one. The installing of software
and downloading of updates are, of course, things that happen rather a lot with a new
PC, and so I think you can guess why I got so agitated over how pointless it would have
been to tell the owner of a shiny new Windows 8 PC to create a Restore Point first.
Configuring System Restore
You should always have System Restore activated on a PC though, and it can be quite common with Windows 11 installations to find that it isn’t activated by default. You can find System Restore most easily by searching for it in the Start Menu and clicking Create a restore point when it appears in the search results. You can also find it in Settings under System ➤ About and labelled as System protection in the related links section.
Tip:System Restore can be run from the Command Prompt or from a PowerShell window by using the command SystemPropertiesProtection and pressing Enter.
With the System Protection panel open on your desktop, you will be able to see if System Restore is configured for each drive or partition you have in your PC. Click the Configure button to set and change its options (see Figure 3-1).
 Figure 3-1. System Restore is simple to configure
Figure 3-1. System Restore is simple to configure
The options need to be changed individually for each disk or partition and include turning System Restore on or off for that disk and assigning how much space on that disk is allocated to the feature. The reason you can configure System Restore for disks other than the one on which Windows is installed dates back to a file versioning feature that was available to Windows File Server administrators back in the days before cloud computing was a thing, and that was later hooked directly into Windows with the File History document and file backup feature; things that in the days of Azure, OneDrive and superfast broadband all now seem incredibly quaint. Suffice to say that System Restore on anything other than your Windows drive serves no purpose these days and isn’t worth activating.
Configuring System Restore Using Scripting
You can also configure System Restore using Power-Shell. Open the Windows Terminal and use the following commands: Enable-ComputerRestore to enable System Restore for a drive with the following switches.
-Drive <String[]> to specify the drive to activate System Restore on, for example, Enable-ComputerRestore -Drive "C:\"
-Confirm to force prompting for confirmation before implementing the change
-WhatIf to show what would happen if the cmdlet runs
Additionally, you can deactivate System Restore for a drive with the DisableComputerRestore command. You can also use Get-ComputerRestorePoint to list the available Restore Points that can be restored and Checkpoint-Computer to manually create a new Restore Point.
If you need to restore a previous backup, use Restore-Computer with the switch -RestorePoint <Int32> where the integer corresponds to the Sequence number of the Restore Point you require and that was displayed using the
Get-ComputerRestorePoint command.
Restoring System Restore Backups
There are several ways to restore your Windows 11 installation to a previous point using System Restore, the first of which uses Power-Shell and that I detailed in the previous section. From the desktop, search in the Start Menu for System Restore and click Create a Restore Point when it appears in the search results.
This will display the dialog we saw earlier, and you can click the System Restore button to start the System Restore operation.
If the PC is unable to start to the desktop, you can run System Restore from the Recovery Console. Click Troubleshoot and then Advanced options, and you will see a System Restore option displayed that will operate just as it does on the desktop.
Tip:System Restore can be run from the Command Prompt or from a Power-Shell window by typing rstrui and pressing Enter.
You will be offered a Recommended restore which will usually be the most recent restore point, but you will also see an option to Choose a different restore point (see Figure 3-2).
 Figure 3-2. The most recent restore point will be displayed as recommended
Figure 3-2. The most recent restore point will be displayed as recommended
When you see the list of available restore points, you might be surprised if there are just one or two available (see Figure 3-3). This is because Windows 11 is, annoyingly, trying to be helpful by giving you the most recent and what it believes are the most relevant points. You might find though that the issue is being caused by software that was installed a few days or even a week or so before. To display all the available restore points, check the Show more restore points box.
 Figure 3-3. Not all available restore points will be displayed
Figure 3-3. Not all available restore points will be displayed
Now you will see a list of all available restore points. Many are deleted when the space available for them is full and needs to be reused. If there is not a lot of general activity on your PC though with updates and software installs, you can find, as seen in Figure 3-4, that the available restore points can helpfully date back a few months.
 Figure 3-4. You can display all available restore points
Figure 3-4. You can display all available restore points
Check the restore point you are interested in using, and then you can click the Scan for affected programs button. Doing so will present a list of all the Win32 programs and drivers installed on your PC that have been installed or updated since that restore point was captured (see Figure 3-5).
 Figure 3-5. You can check what programs will be affected
Figure 3-5. You can check what programs will be affected
Note here that apps installed from the Microsoft Store or from a third-party store will not be included in this list. What is helpfully included though is the version number of the program or driver. This can be especially useful if you are troubleshooting a Windows update and want to roll a specific driver back to a point before an update to that driver made the PC unstable.
With the correct restore point selected, click the Next button to roll the system back to that point. The PC will need to restart to complete this process.
The USB Recovery Drive
One of the biggest problems that can occur with a PC is being unable to boot to the desktop. What’s more, in the worst scenarios you can also hit problems accessing the Recovery Console. This is primarily because Windows 11 boots so quickly; the time you have available to hit the F8 key to access the boot options menu, or Del or F2 to access the UEFI firmware, is incredibly small.
For this reason, I always recommend that you keep a USB Recovery Drive handy. This will not only allow you to boot to the Recovery Console and access the UEFI firmware more easily (additional problems notwithstanding, which I’ll detail later), but it’s also a lot more simple and straightforward to deal with as it was in previous versions of Windows.
I mentioned that sometimes your PC isn’t set to boot from a USB drive. This can be configured in the UEFI firmware in the Boot section. It will display the boot priority for different drives and devices connected to the PC (see Figure 3-6). This may start with your Windows Boot Manager or a specific disk in the PC.
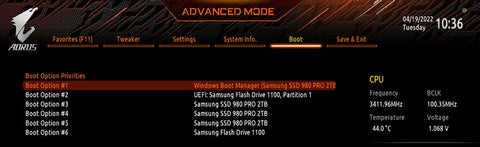 Figure 3-6. You can configure boot priority in the UEFI firmware
Figure 3-6. You can configure boot priority in the UEFI firmware
You can change this boot priority however so that ahead of the Windows Boot Manager is a USB Flash Drive option (see Figure 3-7). This means that if you ever encounter a problem and the PC won’t boot to the desktop, you can very easily start it to a USB Recovery Drive.
 Figure 3-7. You can choose which are the first, second, and third choice boot devices
Figure 3-7. You can choose which are the first, second, and third choice boot devices
USB Drives and Fast Boot
One of the features of modern UEFI motherboards is called Fast Boot, see Figure 3-8. This is a system that lets your PC start much faster than it would normally by initializing all of your hardware at the same time, rather than one device at a time in the way older BIOS systems did it.
 Figure 3-8. Disabling Fast Boot can sometimes be wise
Figure 3-8. Disabling Fast Boot can sometimes be wise
In order for Fast Boot to work, you need a graphics card that supports UEFI GOP (Graphics Output Protocol). One of the disadvantages of Fast Boot however is that it disables the ability to boot the PC from a USB Drive. On my own PCs, I disable Fast Boot as, let’s face it, they boot quickly enough these days anyway, and you might wish to also disable the Fast Boot feature, which can be done from the Boot options if you have a motherboard that supports it.
Creating a USB Recovery Drive
Creating a USB Recovery Drive in Windows 11 is straightforward and takes just a few minutes. It’s also considerably less complicated than with previous Windows versions as I mentioned earlier. The reason for this is that the boot systems of Windows 8, in which the feature first appeared, and earlier versions of Windows 10, had to support BIOS-only motherboards and 32-bit Windows editions.
This meant that the Recovery Drive created would only ever work on that specification, and trying to use a 64-bit Recovery Drive on a 32-bit Windows installation, or a BIOS Recovery Drive on a UEFI system, or the other way around, would result in a PC that wouldn’t start. Fortunately, Microsoft ceased production of 32-bit versions of Windows 10 in May 2020, and Windows 11 won’t install on older BIOS motherboards anyway due to its requirement for TPM 2.0 encryption support.
To create a USB Recovery Drive, search in the Start Menu for recovery and click Recovery Drive when it appears in the search results. The process is simple: plug in a USB Flash Drive (that will be formatted so make sure you don’t need anything on it) of at least 512MB in size and click the Next button (see Figure 3-9).
 Figure 3-9. It is very easy to create a USB Recovery Drive in Windows 11
Figure 3-9. It is very easy to create a USB Recovery Drive in Windows 11
You will see an option to Back up system files to the recovery drive. This will create a copy of the Windows Reset image, which is a feature we’ll look at in Chapter 22. For this backup image to be copied to the drive, you will need a much larger USB Flash Drive, at least 4GB at a minimum.
The reason you might not want to create this image though is that it will date very quickly. In the same way, a System Image Backup, which I will also detail in Chapter 22, will date quickly due to updates and Feature Packs being installed on your PC. You might find that by the time you need to reinstall this image, it’s two or more years old.
File Backup and Restore
I want to put in a note about File Backup and Restore in Windows 11 as it’s still there, but for how long is anybody’s guess. There are two file backup features available, both of them in the Control Panel, Backup and Restore (Windows 7) and File History (see Figure 3-10).
 Figure 3-10. The file backup features of Windows 11 are likely going to be removed
Figure 3-10. The file backup features of Windows 11 are likely going to be removed
Microsoft wants to push people to using its OneDrive file backup and sync service in Windows 11, which is why it will nag you to use it if it’s not set up. As a result, both of these older features have been deprecated for a while and are prime candidates for removal in a future update to the operating system.
It’s not worth therefore showing you how to use these as I feel it would be unwise to encourage you to use a backup system you might later find you’re unable to recover your files from.
OneDrive can be configured to use both a personal and a business account simultaneously. There’s no need in a troubleshooting book to show you how to configure them.
Group Policy
If you use Windows 11 in a workplace environment, then it would be unwise to not set Group Policy for your users. If you’re not aware, Group Policy allows you to set approve or deny permissions and specific configuration options for every aspect of the Windows user experience, from accessing Windows Update and installing drivers to changing the default desktop wallpaper and denying write and copy operations from external media such as USB Flash Drives.
The easiest way to access Group Policy is by typing gpedit at the Start Menu and clicking Edit Group Policy when it appears in the search results. The main Group Policy Editor window is standard Microsoft Management Console (MMC) fare and is unlikely to change during the lifetime of Windows 11 (see Figure 3-11). Figure 3-11. The Group Policy Editor in Windows 11
Figure 3-11. The Group Policy Editor in Windows 11
Policies are split into two separate areas. Computer configuration will set policies that apply to every user on the PC, and User configuration specifies policies that only apply to the currently logged-in user. At the bottom of the windows are Extended and Standard tabs. The Extended view will display a panel containing a verbose description of the policy currently selected, to aid you in setting policies that are correct and appropriate for the user and the PC.
While, as I have said, there are Group Policy options for every single aspect of the PC and user experience, there are some that are particularly helpful when it comes to building a resilient system, and for troubleshooting PCs, and for this I want to give a shout-out to the Microsoft MVP community for submitting their top Group Policy suggestions.
Displaying Detailed Status Messages
If you’re a Windows old-timer like I am, then you might remember that when the operating system started and shut down you would see technical information about what it was doing at the time, such as starting services, loading the user profile, and so on.
These messages can be useful if you need to troubleshoot a problem with startup, shutdown, or with the loading of a user profile and given they don’t slow the system during those operations, and will likely be ignored by the end user anyway you can reactivate them in Windows 11.
Administrative Templates ➤ System ➤ Display Highly Detailed Status Messages is the policy you need to activate to enable this feature, and it will begin displaying them after the next restart of the PC.
Hide Specific Control Panel Items
This is a fairly well-used Group Policy option for corporations and can be used to hide all of the Control Panel applets you don’t want the user to be able to see or access. You can find it in User Configuration ➤ Administrative Templates ➤ Control Panel, and you will need to enter the canonical name for each Control Panel item you wish to hide.
Configure Remote Desktop Access
In Next, we’ll look at how we can use remote access tools to support users in remote locations, and one of the main tools is Remote Desktop. This needs to be activated on PCs and can be done so using Group Policy. Navigate to Computer Configuration ➤ Administrative Templates ➤ Windows Components ➤ Remote Desktop Services ➤ Remote Desktop Session Host ➤ Connections where you can enable remote access of the PC.
Block Inbound Connections for Public Networks
Security can be tightened significantly on a PC by blocking all inbound connections when the computer is connected to a public network, such as a coffee shop or when on a train. Open Computer Configuration ➤ Windows Settings ➤ Security Settings ➤ Windows Defender Firewall with Advanced Security ➤ Windows Defender Firewall with Advanced Security and then click the Windows Defender Firewall Properties link.
This will display a dialog in which you can click the Public Profile tab and block all incoming connections (see Figure 3-12).
 Figure 3-12. Blocking incoming connections for public networks can make a PC more secure
Figure 3-12. Blocking incoming connections for public networks can make a PC more secure
Enable Firewall Logging
Additionally in the Windows Defender with Advanced Firewall policies, you can enable logging for the firewall (see Figure 3-13). This will save a log of firewall activity to a %systemroot%\system32\logfiles\firewall\pfirewall.log file which might be useful later when troubleshooting network issues.
 Figure 3-13. You can enable logging for the Windows Firewall
Figure 3-13. You can enable logging for the Windows Firewall
Disable Removable Storage
One of the main ways for malware to find its way into a corporate network is for it to be brought in by users on a USB Flash Drive. You can disable all removable storage use in Windows 11, and this is also a recommended policy if your servers contain data that might be sensitive to theft.
Computer Configuration ➤ Administrative Templates ➤ System ➤ Removable Storage Access is where you will find the policies for disabling read and write access to a variety of removable storage types including USB Flash Drives, which fall into the Removable Disks category.
Troubleshooting and Diagnostics
This selection of policies, which can be found in Computer Configuration ➤ Administrative Templates ➤ System ➤ Troubleshooting and Diagnostics, contains many policies you might find are useful to implement on your PCs.
They include Application Compatibility Diagnostics which can detect and report different types of Win32 application failure, Corrupt File Recovery, Windows Boot Performance Diagnostics, Windows Memory Leak Diagnosis which can be useful in detecting possible route of attack for malware, and Shutdown, Standby/Resume, and System Responsiveness Diagnostics.
Deactivate AutoPlay
I mentioned a little while ago that you can block all removable media from a PC. You might not want to do this as it can be very useful for users to transfer files to and from USB Flash Drives. Malware can still sit on these drives however, but you can help mitigate against it by deactivating the AutoPlay feature when a drive is plugged in.
Navigate to Computer Configuration ➤ Administrative Templates ➤ Windows Components ➤ AutoPlay Policies to disable the AutoPlay feature for all users on the PC.
Managing Event Logging and Error Reporting
Computer Configuration ➤ Administrative Templates ➤ Windows Components ➤ Event Log Service is where you will find policies for managing the Windows Event Log.
We’ll look at the Event Log in detail in Chapter 8, but it’s an incredibly useful tool for diagnosing problems on a PC. You can manage the Event Log in Group Policy including automatically making backup copies of the event log when it is full.
There are additional error reporting policies to be found in Computer Configuration ➤ Administrative Templates ➤ Windows Components ➤ Windows Error Reporting.
Additional Group Policy Settings
Some of the additional policies you might want to implement can make the PC more secure and less vulnerable to attack by hackers and malware. You can find these in the following locations: Computer Configuration ➤ Administrative Templates ➤ Windows Components, and then select the sub-options for…
- ActiveX Installer Service
- Add Features to Windows 11
- App Package Deployment
- Bio-metrics
- Bit-locker Drive Encryption
- Microsoft Defender Antivirus
- Microsoft Defender Application Guard
- Microsoft Defender Exploit Guard
- Microsoft Secondary Authentication Factor
- Remote Desktop Services
- Windows Installer
- Windows Logon Options
- Windows Remote Management (WinRM)
- Windows Security
- Windows Update
Local Security Policy
In addition to all the control offered by the Group Policy Editor, the Local Security Policy panel provides additional options and control. Most easily accessed from the Start Menu by searching for secpol, the Local Security Policy panel is separated into different easyto-understand categories (see Figure 3-14).
 Figure 3-14. You can specify security policies for the PC
Figure 3-14. You can specify security policies for the PC
These security policies cover all aspects of using and operating the PC. The most useful security policy areas are the following:
- Account Policies is where you can specify minimum password, age, length, and complexity requirements, as well as determine after how many failed login attempts the account is locked on the PC.
- Local Policies contains options for auditing (keeping event logs) account events, as well as specifying security policies for the rights and accesses different users and user groups have on the PC and what types of accounts can be configured.
- Public Key Policies allows you to specify security policies for encryption/decryption keys and data recovery associated with the Encrypting File System (EFS), Data Protection, and Bit-locker.
- Software Restriction Policies allows you to strictly control access to installed software and apps on the PC.
- Application Control Policies is where you can set policies for Microsoft’s App-locker service; this gives system administrators great control over what apps and files can be run and opened and how executable files, scripts, installers, and dynamic-link libraries (DLLs) can open and operate on the PC.
Bio-metrics and Two-Factor Authentication
While we’re on the subject of security, I want to take a little while to talk about the importance of bio-metrics and two-factor authentication (TFA) as both are absolutely crucial in maintaining the data security of businesses and organizations and also the privacy and financial security of absolutely everybody.
There are big differences between the two, and not every method is perfect. You’ll no doubt be aware of what both biometrics and TFA (sometimes referred to as multifactor authentication) are, so I won’t bore you with those details, but I want to highlight some of the real-world problems that we face with these systems and what some of the solutions can be. This is because you might want to take these into account when deciding on what policies to implement for your PCs and systems.
I want to deal with two-factor authentication first as this one drives me absolutely nuts. I live in rural France as I’ve already mentioned earlier in this book. My house has a secondary outbuilding common to France called a gîte. Gîtes are considered holiday homes for visiting guests, but are usually old farm worker accommodation or converted outbuildings. My own gîte used to be a small barn.
Anyway, without wishing to bore you too much with my personal living arrangements, my gîte is where I have put my home office (see Figure 3-15). I did this for two reasons, firstly to keep some kind of separation between my home and work lives and also because (for reasons of it just being healthier this way) I wanted to keep my desktop PC out of the house.
 Figure 3-15. My home office is in my gite
Figure 3-15. My home office is in my gite
So how does this relate to two-factor authentication I hear you ask? The simple fact is that the notifications for TFA alerts almost always come in the form of SMS text messages or pop-ups on my smartphone. “This is perfectly normal, so I’m still not getting it,” you say. I don’t like phones, especially ones that constantly ping, beep, and cry out for my attention. I switch off all notifications and even the call ringer on my smartphones because there’s no message or call that could ever come through that would be so important it couldn’t wait for an hour.
This switching off from my phone means that I don’t habitually carry it around.
Thus, and you’re probably guessing now where this is going, it means that whenever I get a TFA alert, the phone is either in a completely different building to me or is buried away somewhere, forcing me to have to go hunting for it.
A few companies are getting much better at managing TFA alerts. My American Express card is a good example where AMEX gives me a choice of receiving my TFA code by SMS or email. It’s nice, frankly, to have the choice as the number of times I’ve been on my PC in the gîte and had to go stomping back to the house in a bad mood to find my damn phone is too great to count.
So, you say, given that more and more people are switching off from their smartphones and trying to live healthier lives where they’re not constantly connected to the Internet and social media, the answer lies in providing more than one way to receive a TFA alert? Well, yes but with caveats.
The problem here comes with the sending of these alerts by email. Email is the very definition of unsecured communication. It’s unencrypted, easily intercepted, and readable on just about every device we have. Do you have any devices where, once the device is unlocked, you need to enter a password or scan your fingerprint to read your email? Because I don’t, nor do I know anybody that does.
This means that, to take one example, somebody steals your laptop and is able to get to the desktop because you were signed in at the time. They want to perform an action that requires a TFA alert, but rather than also needing access to your smartphone, which is still sitting in your pocket, they can just open your email and get the security code there. Alternatively, the laptop is locked, but they can still get the code as a little preview of the arriving email will appear on the Lock Screen, probably displaying the code in plain text.
Of course, you can prevent the display of email and other incoming messages on the PC’s Lock Screen in Settings ➤ Notifications, and this, frankly, is always a sensible thing to do (see Figure 3-16).
 Figure 3-16. You can hide content from notifications on the Lock Screen
Figure 3-16. You can hide content from notifications on the Lock Screen
The solution comes in the form of bio-metrics. This can be done in one of two ways.
The first is that you have a smartphone set up so that you must use a fingerprint or facial recognition to unlock it every time it’s used, though this can quickly become wearing for the end user and runs the risk of being turned off or reduced to after five or so minutes. The other is to use the Windows Hello bio-metrics system built into Windows 11.
Bio-metrics in Windows currently comes in three different flavors, fingerprint, facial recognition, and smart card, and you can configure Windows Hello in Settings ➤ Accounts ➤ Sign-in options.
Tip:It is widely acknowledged that fingerprint sign-in is more secure than facial
recognition, which can often be fooled by twins or people that look alike and even on occasion by a photograph depending on the system used.
One of the biggest benefits of using Windows Hello is that Microsoft is heavily pushing a passwordless future and is encouraging third-party companies to hook into the biometric systems of your PC. One of the first to hop on board was Google, and you may already have noticed that you can use Windows Hello to authenticate your access to your Google and Google Workspace accounts.
Microsoft also have extensive documentation for how you can use Windows Hello biometrics in your own business or organization, and this goes far beyond what’s available to sign in to an Azure AD or a Microsoft 365 account.
Microsoft’s bio-metrics system has been adopted by other companies and organizations too, including the Fido (Fast IDentity Online) Alliance, which includes hundreds of other members including Apple, Intel, Samsung, and VMware and financial institutions like Visa, American Express, Mastercard, and PayPal. The future of Windows Hello bio-metrics being supported by other companies and organizations will only grow as the years progress.
You can read technical and configuration documentation about using Windows Hello bio-metrics in your own organization on the Microsoft Docs website.
The Windows Security Center
You’ll have probably guessed from reading this chapter, but I have always felt that a significant part of maintaining a robust and resilient PC ecosystem is in setting and maintaining good security, and Windows 11 does indeed include some pretty great security features. In Chapter 18, I’ll show you how to manually remove malware infections from a PC, but even with the main antivirus features switched off and working with live viruses, I was completely unable to infect my test virtual machine. This is clearly a testament to the hard work Microsoft has put in over the last few years.
The Windows Security center is accessible in a few ways. You can search for it in the Start Menu, click the shield icon in the Taskbar System Tray, or open it from Privacy & Security in Settings. I want to make a note here that what you see and what I describe in this section will change over the years. This is both because at the time of writing, Windows Security hasn’t yet had a Windows 11 visual makeover and also because Microsoft is occasionally adding new features and functionality to address the latest threats posed to our PCs.
The main Windows Security center layout though is very unlikely to change, with the main categories for protection listed in a panel on the left side and sub-items for the currently selected panel on the right (see Figure 3-17).
 Figure 3-17. Windows Security is managed from a central panel
Figure 3-17. Windows Security is managed from a central panel
Note:Microsoft does annoyingly use Windows Security to try and push you into using its services, and so you might see some alerts if you don’t have something like OneDrive configured on the PC or if a local account is being used. Hopefully, this is something the company will rectify in the coming years.
Virus and Threat Protection
The main section is where all the anti-malware tools can be found and where you can control the antivirus scanner. There are the usual options available such as quick scan, full scan, custom scan (e.g., for removable media), and also Microsoft Defender Offline Scan which will restart the PC and run a malware scan in the Recovery Environment where no malware can be loaded.
I’m not going to run through all of the anti-malware features, but there are some that are especially noteworthy I want to draw attention to.
Excluded Items
One of the challenges with troubleshooting virus and malware issues can be the problem of false-positives. These can come from a variety of sources. You might, as an example, have older visual basic or other macro scripts that you need to use in your workflow, where those workflows haven’t been transitioned to newer methods yet or where it’s simply not feasible to do so.
You will likely know that scripts and macros are a great place for malware to hide, and for many years, Word, Excel, PowerPoint, and Adobe Portable Document Format (PDF) files were targeted by malware writers or distributed by them via email to try and spread infection.
As a result, the companies combating malware, Microsoft included, built safeguards into their software which, naturally, greatly increased the likelihood of getting a falsepositive result on a nonmalware-infected file that you need or use in your daily workflow.
In the main Windows Security panel, under the Virus & threat protection section, you can add (and remove) exclusions for a PC (see Figure 3-18). This means you can tell Windows Security not to scan files it is flagging as infected incorrectly.
 Figure 3-18. You can exclude false-positive files from malware scans
Figure 3-18. You can exclude false-positive files from malware scans
Tip:You can roll out global configuration for Windows Security across your organization, including adding file exclusions, by using the Group Policy Editor. You will find all the available options under Computer Configuration ➤ Administrative Templates ➤ Windows Components ➤ Microsoft Defender Antivirus.
Controlled Folder Access
Just above Excluded items in the Virus & threat protection center is a feature called Controlled Folder Access (see Figure 3-19). This is a highly useful and highly effective feature for combating ransomware, and if you use Windows Security antivirus on your PCs as opposed to a third-party solution, then I thoroughly recommend you activate it.
 Figure 3-19. Windows 11 has ransomware protection baked-in
Figure 3-19. Windows 11 has ransomware protection baked-in
What Controlled Folder Access does is monitor the user folders on a PC (Documents, Pictures, etc.) and block any attempt from a process or service it doesn’t recognize that tries to make a change. These changes include modifying a file to inject malware, encrypting or changing it, or deleting it.
Where Controlled Folder Access can cause problems is where you have third-party software that legitimately needs to access the protected folders, but that isn’t recognized by the feature, or where you need an additional folder or folders on the PC protected by the feature, such as a file store on a second internal hard disk or SSD.
The first problem is very common for gaming PCs, where the games need access to the file stores. If an app is blocked from making changes to the protected folders, a popup alert will appear in the bottom-right corner of the desktop, telling you that “unwanted changes were blocked.” This, fortunately, is both very easy to fix and only has to be fixed once.
In the Controlled Folder Access settings in Windows Security, there are four options available to you. The first is a simple on/off toggle switch for the feature. Below this, you will see links to display your Block history, to set your Protected folders, and to Allow an app through controlled folder access (see Figure 3-20).
 Figure 3-20. You can manage Controlled Folder Access in Windows Security
Figure 3-20. You can manage Controlled Folder Access in Windows Security
To add a folder or indeed a full drive to Controlled Folder Access, click the Protected folders link where you will be able to add (or remove) folders from monitoring. If you need to allow an app through, then click the Allow an app through… link where you will be able to add it.
On many occasions however, an app will be blocked, you won’t really know what it is, and perhaps the pop-up notification telling you (or another user you are supporting) disappeared from the desktop before they could properly read it.
This is where the Block history comes in useful. Click this and you will see a list of events that were blocked by Controlled Folder Access. Click one to expand it and view more information, and you will see details about the date and time the event occurred, as well as the name of the app or process that was blocked, and the protected folder it tried to access (see Figure 3-21).
 Figure 3-21. You can view the block history for Controlled Folder Access
Figure 3-21. You can view the block history for Controlled Folder Access
If you recognize something as an app or process that should not have been blocked, click the Actions button, and an option will appear to Allow [that app] on [the] device.
Just clicking this once will set the exclusion globally, and you won’t have to worry about it again on that PC.
Bear in mind however that some apps have several different processes that need to access. It can be wise to keep a list of which apps need to be allowed through. You can then configure this globally for your organization using Group Policy. Navigate in the Group Policy Editor to Computer Configuration ➤ Administrative Templates ➤ Windows Components ➤ Microsoft Defender Antivirus ➤ Microsoft Defender Exploit Guard ➤ Controlled Folder Access, and you will see an option to Configure allowed applications along with other global controls for the feature (see Figure 3-22).
 Figure 3-22. You can configure Controlled Folder Access using Group Policy
Figure 3-22. You can configure Controlled Folder Access using Group Policy
Reputation-Based Protection
Microsoft has for a few years now included in Windows a cloud protection feature called Smart-screen. What this does is check downloaded files and apps against white and black lists held by Microsoft. These lists are compiled collaboratively between Microsoft and many other operating system and security firms. If a file or an app is being downloaded that appears suspicious, then it will be automatically blocked by the system.
Again, this can be problematic in business where you might occasionally or even regularly need to share older apps and files that aren’t on the white list. To fix this, open Windows Security and navigate to App & browser control, where you will see a Reputation-based protection settings link (see Figure 3-23).
 Figure 3-23. You can manage Windows Smart-screen in Reputation Protection
Figure 3-23. You can manage Windows Smart-screen in Reputation Protection
There’s no real reason to ever disable Smart-screen, though if you host installers and documents on your company network that are flagged by the system as false-positives, or you already have a Sonic-Wall or similar appliance that does much the same job, it can be disabled.
Microsoft has a facility where you can submit files that are being incorrectly reported, so they can be added globally to the Smart-screen white list.
Additionally, if you need to check what files have been blocked by Smart-screen, you can use the Power-Shell command wevtutil sl Microsoft-Windows-Smart-screen/ Debug /e:true to display the full Smart-screen log for a PC.
Exploit Protection
The other security settings I want to highlight are under App & browser control and Exploit protection (see Figure 3-24). These include settings that are more closely linked to your PC’s hardware, such as the processor and memory, and they exist to prevent events like memory buffer overflows that can be used to inject malware into a system.
 Figure 3-24. Exploit protection settings are more closely linked to your processor and physical memory
Figure 3-24. Exploit protection settings are more closely linked to your processor and physical memory
Where you might need to configure this is if you are using older, custom software written for a specific purpose at your organization. This can frequently use programming techniques that are frowned upon today, such as always requiring administrator privileges to work, which was common back in the days before Vista.
Click Program setting and you can add and edit override settings for specific applications that are blocked by Windows 11’s security or do not function correctly (see Figure 3-25).
 Figure 3-25. You can override exploit protection for specific apps
Figure 3-25. You can override exploit protection for specific apps
Additionally, in the Exploit protection settings is an Export settings link. You can use this when you have configured all of your required overrides to save your configuration as an XML file that can then be rolled out across your organization. It’s not immediately obvious in Windows Security how you do this, but Microsoft provides a full guide on its Doc website including how you can use Power-Shell to automate the export and deployment process.
Device Security
An additional memory integrity option exists in Device security ➤ Core isolation though this is disabled by default because it can interfere with the operation of some older apps.
Core isolation helps prevent malware from inserting code into high-security memory processes by virtualizing some parts of the Windows and app operation on the PC.
This is, of course, a highly useful security feature, though you will need to thoroughly test all of your bespoke and mainstream apps to make sure they won’t be broken by its security. There is a Learn more link in the Core isolation settings page that takes you directly to a Microsoft website that provides more in-depth and up-to-date information about this feature.
Protection History
The last part of Windows Security I want to highlight is the Protection history link at the bottom of the main menu list (see Figure 3-26). This is an easy-to-access panel that will display all the security events that have been blocked by Windows Security, and it’s a useful “quick find” location if you want to determine if settings need to be tweaked or an app allowed through a security feature.
 Figure 3-26. You can easily access your Protection History in Windows Security
Figure 3-26. You can easily access your Protection History in Windows Security
The Windows Advanced Firewall
Windows 11 includes two different firewall interfaces. The main firewall is available in Windows Security under Firewall and network protection. This is a fairly basic interface all told as the Windows Firewall rarely needs any real configuration; it’s just something that sits quietly in the background and that works so effectively that many third-party antivirus companies have long since abandoned their own bundled firewalls.
At the bottom of the Firewall & network protection panel however are some useful links (see Figure 3-27). The most useful of these is to Allow an app through the firewall. This currently takes you to a Control Panel applet, but it’s something that will be folded completely into settings at a future time.
 Figure 3-27. You have basic control of the Firewall in Windows Security
Figure 3-27. You have basic control of the Firewall in Windows Security
If you click the Advanced settings link, then Windows Defender Firewall with Advanced Security, otherwise known as the Advanced Firewall interface, will open (see Figure 3-28). Note that you can also find the Advanced Firewall in Windows Tools.
 Figure 3-28. The Advanced Firewall offers full firewall control and configuration
Figure 3-28. The Advanced Firewall offers full firewall control and configuration
It is in this interface that you can configure custom rules such as allowing or blocking specific ports on the PC or specifying that network and Internet connections of certain types must always be encrypted.
Note: Windows Defender Firewall with Advanced Security is also available in the Group Policy Editor under Computer Configuration ➤ Windows Settings ➤ Security Settings ➤ Windows Defender Firewall with Advanced Security.
Under the Action menu in the Advanced Firewall, you will find Import and Export options which will use *.wfw files which are binary Registry Hive files. These can be opened using the Registry Editor in Windows. Make certain though that you first create a new Registry key to import the Hive into; otherwise, you might find yourself overwriting rules on the PC you would rather not be touched. You should delete your temporary Registry key when you are finished. As you might imagine, the Firewall can be configured using Power-Shell.
Troubleshooting and Repairing the Windows Firewall
You can troubleshoot and reset the Windows Firewall in both Windows Security and the Advanced Firewall panels. In the former, click the Restore firewalls to default link. In the Advanced Firewall, click the Action menu and you will see options to Restore Default Policy and Diagnose/Repair.
The latter of these will run one of Windows 11’s automated troubleshooters. These reset Windows components to their default state if they are found to be corrupt or not working correctly. The former option will simply reset the firewall to how it was when Windows 11 was first installed.
Summary
There are a lot of features available in Windows 11 to help safeguard against problems occurring in the future, and the security features are indeed extensive. We can expect these security options to be changed and expanded on over time as new types of threat emerge, so it’s possible that what I have described in this chapter could be different a few years down the line.
What is clear however is that correctly configuring Windows 11 is key to a happy and productive time using your PCs, so in the next chapter we’ll examine how to do this from managing user accounts and shell user folders to helping hybrid workers and creating sustainable PC systems.




